Our Services
We deliver reliable 24/7 support and adhere to industry standards such as HIPAA, PCI DSS, and GDPR to ensure robust data security. Our services are designed to strengthen compliance with critical regulations such as ISO 27001, GDPR, and more. We offer customizable dashboards that provide comprehensive visibility into regulatory reporting and compliance management. These dashboards help streamline the monitoring process, ensure adherence to industry standards, and simplify audits, empowering organizations to meet evolving regulatory requirements with confidence and efficiency.
Security Audit
Our Security Audit services are designed to identify vulnerabilities and gaps in your IT infrastructure, while also adhering to industry regulations and internal policies. We give you actionable insights to enhance your organization's security posture.
Protect, Detect, and Respond with our comprehensive cybersecurity services, tailored to meet the unique needs of your business. Reach out to us to enhance your cybersecurity and stay ahead of evolving threats.
- Comprehensive security
- assessment Vulnerability
- scanning Penetration testing
- Risk assessment
Shared CISO
- Expert guidance
- Regular Assessments
- Compliance support
- Threat Intelligence
- Incident Response Planning
- Disaster recovery planning
- Security Hardening
Risk Assessment
- Comprehensive coverage
- Threat modeling
- Business impact analysis
- Recommendations and remediation plans
24/7 SOC
- Log management
- Real-time monitoring
- Incident response
- Threat detection
- Network Security Deployment
- Endpoint Protection service
- Compliance reporting
- Customizable dashboards and reports
VAPT
- Comprehensive coverage
- Automated scanning
- Identification of risks
- Vulnerability identification
- Reporting & Patch management
- Recommendations and remediation plans
- Use of industry-standard testing methodology
Next Gen SIEM
Our Next Generation Security Information and Event Management (SIEM) solution provides a solution that enables us to monitor in real time, detect advanced threats, and respond to incidents automatically. We minimize risks by identifying and prioritizing potential threats by analyzing logs from diverse sources. The solution enhances compliance and regulatory reporting by providing customizable dashboards that provide clear visibility.
Security Operations Center (SOC)
Our SOC is operational 24/7 and provides instant threat detection and incident response. Continuous surveillance of your infrastructure is ensured by our around-the-clock monitoring service, which detects and responds to threats in real-time. The SOC is equipped with experienced security professionals and advanced tools to quickly detect and neutralize threats. Our experts mitigate risks before they turn into incidents .
Threat Intelligence
Our Threat Intelligence service is designed to keep you informed about emerging threats by giving you actionable insights into vulnerabilities, adversaries' tactics, and global cybersecurity activity. Strategic security decisions can be improved by tailoring threat alerts to enhance incident response and vulnerability management.
Proactive Threat Hunting
Our security analysts constantly search for hidden threats within your network, using advanced techniques to detect and eliminate risks before they lead to breaches or attacks, improving your overall security.
Prevent, Detect & Respond
By utilizing proactive security controls to prevent attacks, real-time detection of anomalies through advanced intelligence, and expert incident response, we ensure that damage is mitigated. Your security posture is strengthened, and downtime is minimized by this comprehensive approach.
Integration with Security Tools
Enhance the efficiency of your existing security tools with expert integration. We make sure that security operations are seamless, and threat management is enhanced by connecting and optimizing SIEM, IAM, IDS/IPS, and other solutions.
Network & Endpoint Monitoring
Our service provides real-time visibility into network and endpoint activity, as well as detecting unauthorized access, system compromises, and malicious behavior. The risk of data breaches can be minimized, and compliance is assured through this comprehensive monitoring.
Case Study
Problem statement
- Need for Continuous Uptime: Critical systems and applications required 24/7 availability to meet customer expectations and business needs.
- Limited Visibility: Lack of real-time monitoring tools made it difficult to detect and resolve infrastructure issues quickly.
- Inefficient Incident Management: Without a centralized system, managing incidents and service requests was time-consuming and prone to errors.
- Resource Constraints: Manual processes and lack of automation increased the workload on the IT support team.
Solutions
- 24/7 Security Operations Center (SOC):Deployed AlienVault USM for round-the-clock security monitoring and automated threat response.
- Cybersecurity Vulnerability Management:Conducted regular scans, prioritized vulnerabilities, and managed remediation efforts.
- Endpoint Detection and Response (EDR): Implemented advanced EDR tools for real-time monitoring and threat mitigation on endpoints.
Key Points
- 100% Faster Threat Detection and Response: Achieved with continuous SOC monitoring.
- 75% Reduction in Critical Vulnerabilities: Through proactive vulnerability management.
- 50% Decrease in Endpoint Security Incidents: Enabled by EDR tools.
- 40% Improvement in Incident Management Efficiency: Due to automation and streamlined processes.
Technologies
- AlienVault USM: For SOC operations, providing SIEM, threat detection, and automated response.
- EDR Tools: For comprehensive endpoint monitoring and real-time threat detection.
- Vulnerability Scanning Solutions: For regular assessments and prioritization of vulnerabilities.
Partnership and Certifaction
We, as a Level Blue Managed Security Service Provider (MSSP), are dedicated to providing advanced cybersecurity services to protect your organization from evolving threats. Our team comprises CEH and ISACA's CISM professionals who are experts in security management and ensure compliance with industry regulations.

Risk Assessment Process
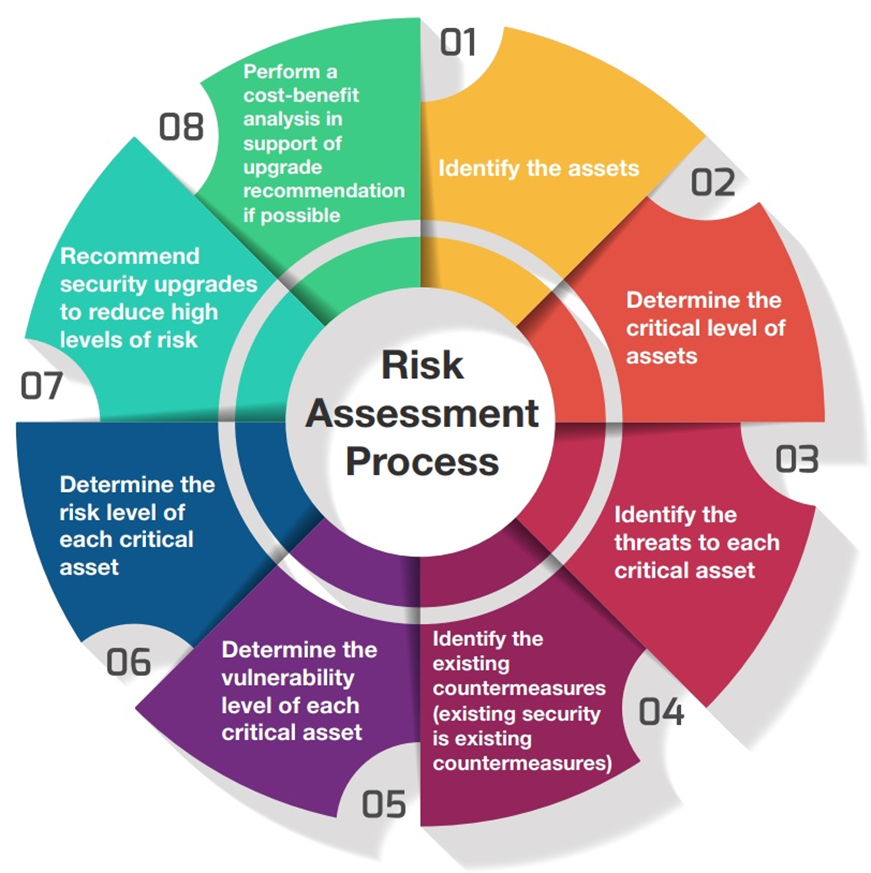
- Identify the assets
- Determine the critical level of assets
- Identify the threats to each critical asset
- Identify the existing countermeasures (existing security is existing countermeasures)
- Determine the vulnerability level of each critical asset
- Determine the risk level of each critical asset
- Recommend security upgrades to reduce high levels of risk
- Perform a cost-benefit analysis in support of upgrade recommendation if possible
SECURITY OPERATIONS CENTER (SOC)
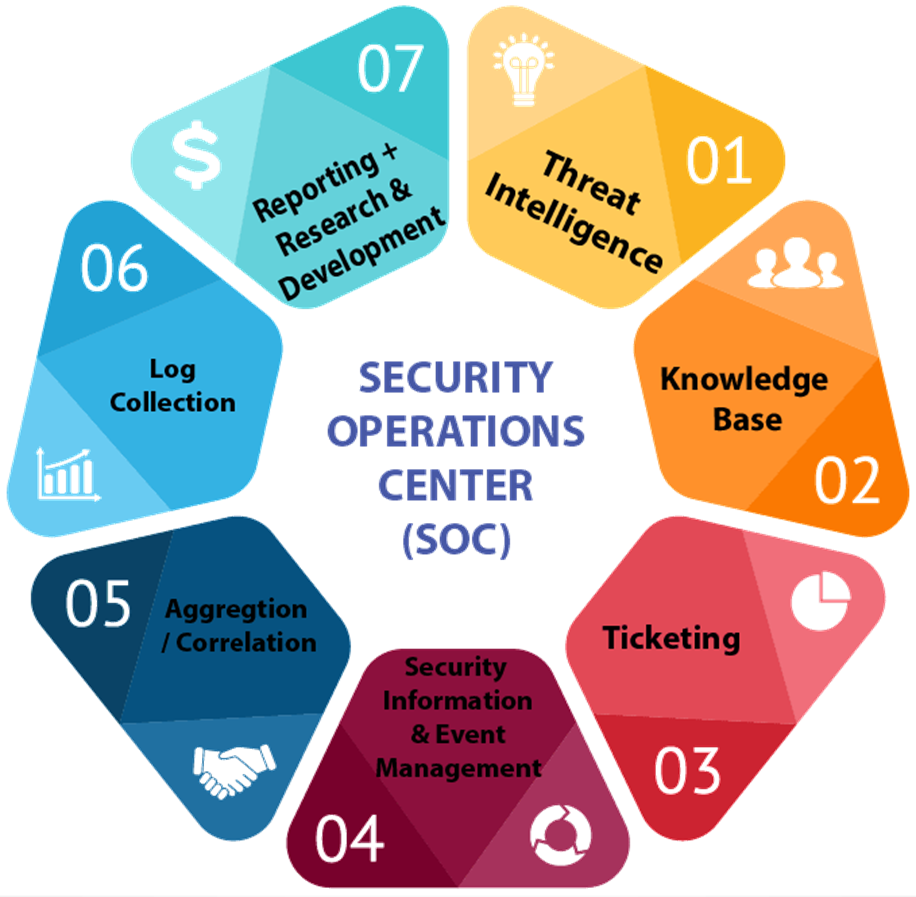
- Threat Intelligence
- Knowledge Base
- Ticketing
- Security Information & Event Management (SIEM)
- Aggregation / Correlation
- Log Collection
- Reporting + Research & Development
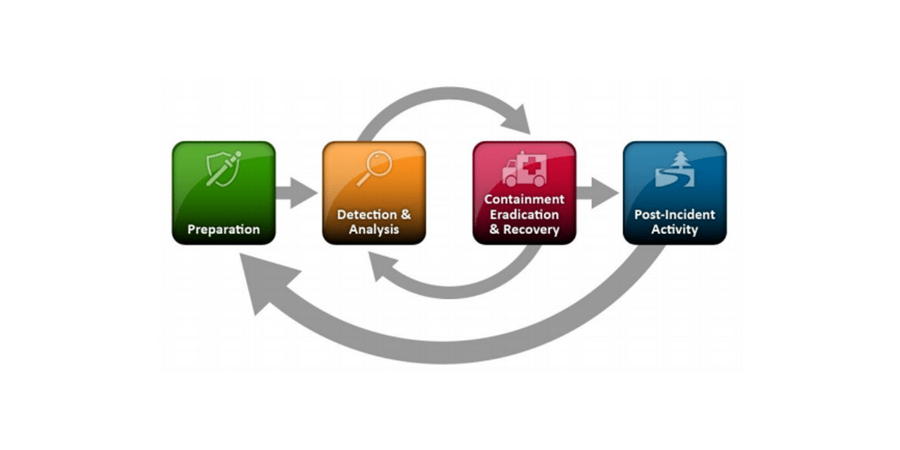
Incident Response Life Cycle